
The Industrial Internet of Things (IIoT) has become an essential aspect of Industry 4.0, with smart devices now a common sight in various industries. According to the Industrial Internet Consortium (IIC), only 25% of organizations have a clear lloT security strategy. Leaders are struggling most with data security (51%) and privacy (39%). Overcoming these barriers is essential to the success of the lloT.
The growing adoption of IIoT also brings about an increased risk of security breaches, as evidenced by the notorious Triton malware attack, which targeted safety systems in industrial facilities.
The Triton malware attack, also known as TRISIS or HatMan, was first discovered in 2017. This sophisticated cyberattack targeted industrial safety systems at a petrochemical plant in Saudi Arabia. Triton specifically targeted Triconex Safety Instrumented System (SIS) controllers, which are designed to ensure safe operations in industrial environments by shutting down processes when they detect dangerous conditions.
The attackers were able to infiltrate the plant's network and gain access to the SIS controllers, modifying their configurations to potentially cause catastrophic physical damage. Fortunately, an error in the attackers' code inadvertently triggered the plant's safety systems, causing the facility to shut down before any significant harm could occur. This incident highlighted the growing threat to critical infrastructure and the potential consequences of successful cyberattacks on IIoT systems.
Although the Triton attack did not result in a large-scale disaster or loss of life, it demonstrated the vulnerability of industrial control systems and the potential for devastating impacts. If the attack had succeeded, it could have led to a major accident involving loss of life, significant environmental damage, and severe financial losses. This incident serves as a stark reminder of the importance of robust IIoT security measures and the need to continuously assess and improve the resilience of industrial systems.

This blog explores how IIoT is being integrated into production systems, its challenges and risks, and the best practices for ensuring security and resilience.
As industries evolve, IIoT capabilities have proven invaluable in creating new production systems that leverage remote control, monitoring, and increased network speeds and processing power to transform traditional manufacturing processes.

Companies have integrated remote control and monitoring systems into their production lines, allowing for more efficient oversight and reducing the need for human intervention. These systems have streamlined operations, increased productivity, and improved overall performance.
Developing advanced networking capabilities and faster processing power has enabled IIoT devices to handle larger workloads and process data more efficiently. This has improved response times, accurate data analysis, and decision-making.


Siemens has further integrated IIoT by offering fully automated smart factories and IIoT as a service. This approach allows companies to benefit from faster production processes and data-driven insights. Artificial intelligence and machine learning algorithms analyze the data collected by these systems, leading to continuous improvements in production efficiency.
One of the ways IIoT can provide additional value is by monitoring and improving the performance of older systems. Retrofitting existing equipment with networkable devices can significantly improve efficiency and cost savings.
By retrofitting old devices with new networkable equipment, companies can turn their systems' potential flaws into production benefits. This can be achieved by adding monitoring devices to existing systems, such as a brewery's bottling line, or connecting devices to Programmable Logic Controllers (PLCs) to read and transmit data through standard ICS protocols like MQTT or REST.
Two common methodologies are used in retrofitting: integrating new devices into the system at the same level as a Human Machine Interface (HMI) or the logic level, tracking and monitoring information across various channels. These approaches allow for more effective monitoring and control of older systems while maintaining security and minimizing vulnerabilities.
As the integration of IIoT devices grows, it is essential to address the risks and challenges associated with the expanding attack surface for potential cyber threats.

Even with air-gapped systems, attackers can access IIoT devices and cause disruptions or damage. Data collection errors, loss of connection, and malicious insider activity can all lead to compromised systems. Furthermore, intercepted communications between IIoT devices and gateways can reveal sensitive information or enable attackers to manipulate devices.
Introducing IIoT devices can also increase the risk of malware attacks, such as the Triton incident targeting production lines' safety systems. Apart from the potential loss of human life, downtime caused by these incidents can result in significant financial damage.
Another concern for organizations implementing IIoT technology is the possibility of device failure. Ensuring redundancy and preparing for potential device failures is crucial to maintain production continuity and protect against unexpected downtime.
As data is collected and transmitted by IIoT devices, and there is a risk of interception and exposure of sensitive information, such as trade secrets or production processes. Organizations must protect their data and intellectual property to avoid potential losses.
Despite the risks and challenges of IIoT implementation, proper security management and best practices can mitigate threats and protect production systems.
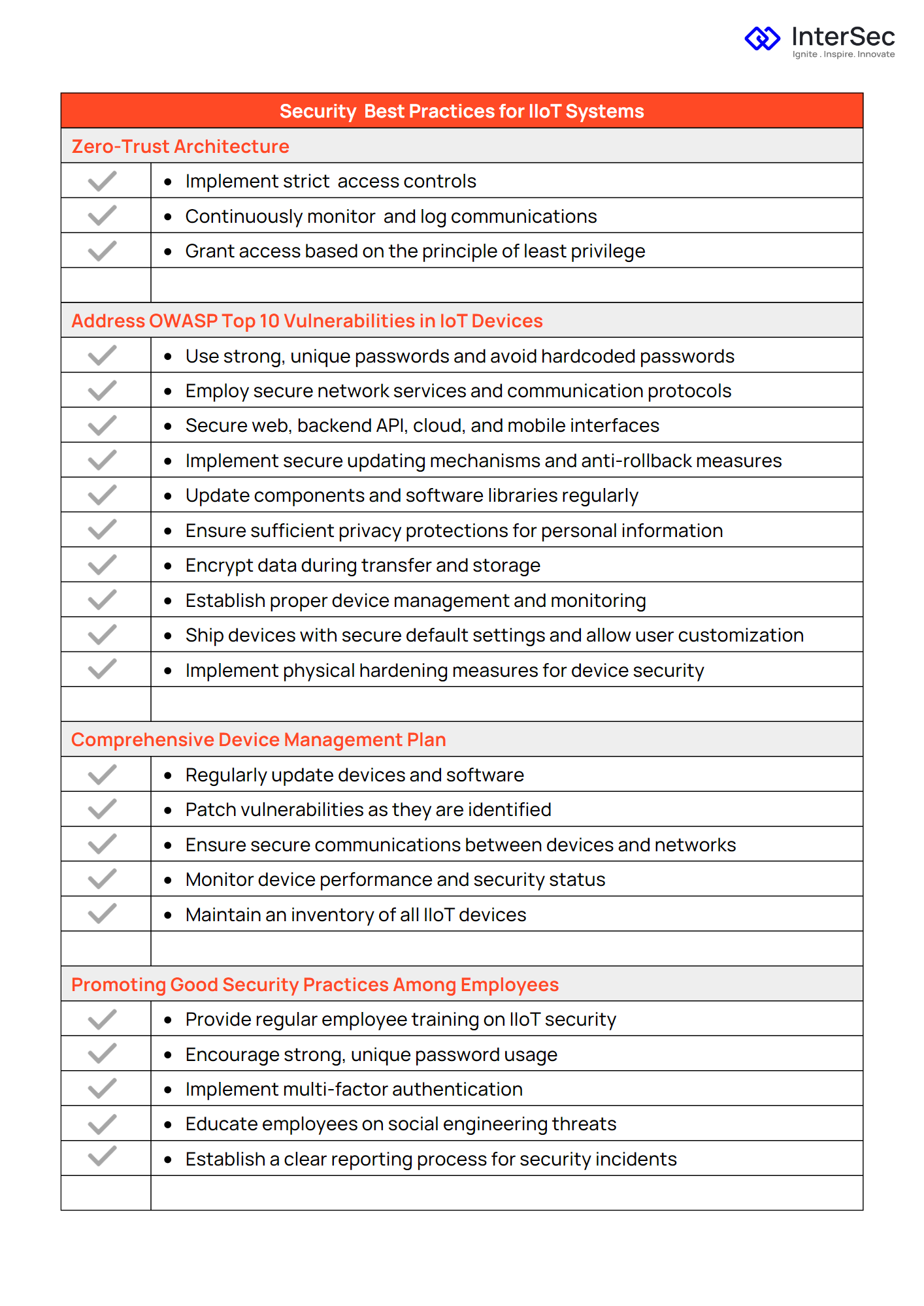
Embracing a Zero-Trust Architecture can help secure IIoT systems. Organizations can minimize the risk of unauthorized access and potential attacks by granting access only to those with a legitimate need and closely monitoring communications between IIoT devices and external systems.

The OWASP IOT Top 10 risks provide a valuable framework for securing IIoT devices. By addressing these risks and implementing appropriate security measures, organizations can improve the overall security of their IIoT systems. https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf

A well-rounded device management plan is essential for maintaining the security and functionality of IIoT devices. This includes regular updates, patching vulnerabilities, and ensuring secure communications between devices and networks.
Employee training and awareness is vital to maintaining the security of IIoT systems. Organizations should educate employees on the importance of using strong, unique passwords and following best practices for protecting company data and devices.
In conclusion, the integration of IIoT devices in Industry 4.0 offers numerous opportunities for increased efficiency, productivity, and innovation. By adopting best practices for security and device management, organizations can harness the power of IIoT while maintaining the safety and resilience of their production systems. The associated risks and challenges also demand a robust and comprehensive cybersecurity strategy.
InterSec Inc, as a leading cybersecurity services provider, offers a wide range of solutions specifically designed to address the unique security needs of IIoT systems. We have helped many companies secure their IIOT systems.
With our extensive experience and expertise in securing industrial systems, we can also help you navigate the complex landscape of IIoT security. Our services include vulnerability assessments, penetration testing, zero trust architecture implementation, and employee training programs. By partnering with InterSec Inc, your organization can not only mitigate potential threats but also maintain the safety and resilience of your production systems.
As the industrial landscape continues to evolve, trust InterSec Inc to stay ahead of emerging threats and provide cutting-edge cybersecurity solutions tailored to your IIoT infrastructure. Together, we can ensure your organization reaps the full benefits of Industry 4.0 while safeguarding your valuable assets and maintaining a secure and resilient environment.